Logic gates play a crucial role in security systems by enabling the implementation of complex decision-making processes. These electronic circuits are responsible for processing and manipulating binary signals, allowing security systems to perform various functions such as authentication, access control, and alarm triggering. Logic gates, including AND, OR, NOT, and XOR gates, are used to combine and manipulate input signals to produce desired output signals. By utilizing logic gates, security systems can evaluate multiple inputs and make informed decisions based on predefined conditions. These gates form the foundation of secure and reliable security systems, ensuring the protection of assets and individuals.
Key Takeaways
| Logic Gate | Function |
|---|---|
| AND | Performs logical AND operation on inputs |
| OR | Performs logical OR operation on inputs |
| NOT | Inverts the input signal |
| XOR | Performs exclusive OR operation on inputs |
Understanding Logic Gates
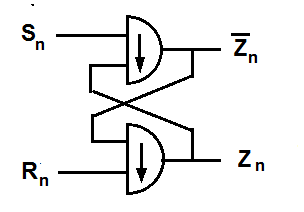
Logic gates are fundamental building blocks of digital circuits. They are electronic devices that perform logical operations on one or more binary inputs to produce a single binary output. Logic gates play a crucial role in various aspects of technology, including security systems, encryption, access control, and more. In this article, we will explore the definition and function of logic gates, how they work, and their real-life applications.
Definition and Function of Logic Gates
Logic gates are electronic circuits that operate on binary inputs (0s and 1s) based on Boolean algebra. They are designed to perform specific logical operations, such as AND, OR, NOT, XOR, NAND, and NOR. Each logic gate has a unique truth table that defines its behavior. The truth table specifies the output value of the gate for all possible combinations of input values.
Here are some commonly used logic gates and their functions:
- AND Gate: The AND gate produces a high output (1) only when all of its inputs are high (1). Otherwise, it produces a low output (0).
- OR Gate: The OR gate produces a high output (1) if any of its inputs are high (1). It produces a low output (0) only when all of its inputs are low (0).
- NOT Gate: The NOT gate, also known as an inverter, produces the opposite output of its input. If the input is high (1), the output is low (0), and vice versa.
- XOR Gate: The XOR gate, or exclusive OR gate, produces a high output (1) if the number of high inputs is odd. Otherwise, it produces a low output (0).
- NAND Gate: The NAND gate is a combination of an AND gate followed by a NOT gate. It produces the opposite output of an AND gate.
- NOR Gate: The NOR gate is a combination of an OR gate followed by a NOT gate. It produces the opposite output of an OR gate.
Logic gates can be combined to create more complex circuits and perform various logical operations. They are the building blocks of digital systems and are used extensively in computer networks, information security, data protection, and other areas.
How Logic Gates Work
Logic gates work based on the principles of Boolean algebra. They operate on binary inputs and produce a binary output based on the logical operation defined by their truth table. The inputs and outputs of logic gates are represented by binary values, where 0 represents a low voltage level and 1 represents a high voltage level.
To understand how logic gates work, let’s take a look at the truth table of an AND gate:
| Input A | Input B | Output |
|---|---|---|
| 0 | 0 | 0 |
| 0 | 1 | 0 |
| 1 | 0 | 0 |
| 1 | 1 | 1 |
As per the truth table, the AND gate produces a high output (1) only when both of its inputs are high (1). Otherwise, it produces a low output (0). This behavior is achieved through the use of transistors and electronic components that implement the logical operation.
Logic gates can be implemented at the gate level using transistors or at a higher level using integrated circuits. Integrated circuits, such as logic gates, are commonly used for their compact size, reliability, and ease of use.
Real-life Applications of Logic Gates
Logic gates have numerous real-life applications in various fields, including:
- Security Systems: Logic gates are used in security systems for tasks such as access control, authentication, and authorization. They help ensure that only authorized individuals can gain access to secure areas or sensitive information.
- Encryption and Decryption: Logic gates are used in encryption and decryption algorithms to secure data transmission and protect sensitive information. They play a vital role in ensuring the confidentiality and integrity of data.
- Biometric Systems: Biometric systems, such as fingerprint scanners and facial recognition systems, use logic gates to process and compare biometric data for identification and verification purposes.
- Intrusion Detection Systems: Logic gates are used in intrusion detection systems to analyze network traffic and detect any unauthorized or suspicious activities. They help protect computer networks from potential threats.
- Firewalls: Firewalls use logic gates to filter and control network traffic based on predefined rules. They help prevent unauthorized access and ensure the security of computer networks.
- Secure Communication: Logic gates are used in secure communication protocols to encrypt and decrypt data, ensuring that it remains confidential during transmission.
- Information Security: Logic gates are essential in information security systems, including data protection, access control, and secure communication, to safeguard sensitive information from unauthorized access or manipulation.
- Computer Networks: Logic gates are used in the design and implementation of computer networks to perform routing, switching, and other network operations.
- Cyber Security: Logic gates play a crucial role in various aspects of cyber security, including intrusion detection, data protection, secure communication, and network security.
- Gate-level Implementation: Logic gates are used in the gate-level implementation of digital circuits, where they are combined to create more complex circuits and perform specific functions.
- Boolean Algebra and Circuit Design: Logic gates are an integral part of Boolean algebra and circuit design. They enable the creation of logical expressions and the design of digital circuits for various applications.
The Role of Logic Gates in Security Systems
Logic gates play a crucial role in the functioning of security systems, ensuring the protection of sensitive information, physical assets, and individuals. These gates are fundamental building blocks of digital circuits and are used extensively in various aspects of security, including encryption, decryption, access control, authentication, and authorization.
Logic Gates in Electronic Security Gate Systems
Electronic security gate systems rely on logic gates to control access and enhance security. These gates are responsible for processing input signals from various sensors and determining whether to grant or deny access. By using gate-level implementation and Boolean algebra, these systems can accurately evaluate the conditions for access and make informed decisions.
Logic gates enable the implementation of complex access control mechanisms in electronic security gate systems. They can combine multiple inputs, such as biometric systems, keycards, or passwords, and apply logical operations to determine if the access request is valid. This gate-level implementation ensures that only authorized individuals can enter restricted areas, enhancing the overall security of the premises.
Use of Logic Gates in Burglar Alarm Systems
Burglar alarm systems utilize logic gates to detect and respond to unauthorized entry attempts. These systems rely on sensors, such as motion detectors and door/window sensors, to detect any intrusion. Logic gates process the signals from these sensors and trigger an alarm if the conditions for unauthorized entry are met.
By using truth tables and circuit design, logic gates in burglar alarm systems can accurately evaluate the input signals and determine if an intrusion is occurring. These gates can be programmed to consider various factors, such as the time of day or the presence of authorized personnel, to minimize false alarms and ensure reliable detection.
Logic Gates and Logical Access Control
Logic gates also play a vital role in logical access control systems, which are used to secure computer networks, information systems, and data. These systems rely on logic gates to evaluate the authentication and authorization of users, ensuring that only authorized individuals can access sensitive information.
By using logic gates, access control systems can compare user credentials, such as usernames and passwords, with stored data to verify the user’s identity. These gates can perform logical operations to determine if the provided credentials match the authorized access rights, granting or denying access accordingly.
Furthermore, logic gates are used in the implementation of firewalls and secure communication protocols. These gates evaluate incoming network traffic and apply logical rules to allow or block data packets based on predefined security policies. By utilizing logic gates, these systems can effectively protect against unauthorized access and ensure the confidentiality and integrity of data.
Logical Security: An Overview
Logical security is a crucial aspect of information security that focuses on protecting data and resources through the implementation of various controls and policies. It involves safeguarding the logical components of a system, such as software, networks, and data, from unauthorized access, manipulation, or destruction. By employing a combination of security measures, logical security helps to ensure the confidentiality, integrity, and availability of sensitive information.
Definition and Importance of Logical Security
Logical security encompasses a wide range of measures designed to protect digital assets from both internal and external threats. It involves the use of security systems, protocols, and technologies to mitigate risks and prevent unauthorized access to sensitive data. The role of logical security is to establish a secure environment by implementing controls that govern access, authentication, authorization, and data protection.
One of the fundamental concepts in logical security is the use of encryption and decryption techniques. Encryption involves converting data into an unreadable format using cryptographic algorithms, while decryption is the process of converting the encrypted data back into its original form. This ensures that even if unauthorized individuals gain access to the data, they cannot understand or utilize it without the proper decryption key.
Access control is another critical aspect of logical security. It involves managing and controlling user access to resources based on their roles and privileges. By implementing access control mechanisms, organizations can ensure that only authorized individuals can access specific information or perform certain actions. This helps prevent unauthorized users from tampering with sensitive data or systems.
Authentication and authorization are also essential components of logical security. Authentication verifies the identity of users attempting to access a system or resource, typically through the use of passwords, biometric systems, or multi-factor authentication. Authorization, on the other hand, determines the level of access and permissions granted to authenticated users. By implementing robust authentication and authorization mechanisms, organizations can ensure that only authorized individuals can access critical resources.
Examples of Logical Security Controls
There are various logical security controls that organizations can implement to protect their digital assets. Some common examples include:
Intrusion Detection Systems (IDS): These systems monitor network traffic and identify any suspicious or malicious activities. They can detect and alert administrators about potential security breaches, allowing them to take appropriate actions to mitigate the risks.
Firewalls: Firewalls act as a barrier between internal networks and external networks, such as the internet. They examine incoming and outgoing network traffic and enforce security policies to prevent unauthorized access and protect against network-based attacks.
Secure Communication Protocols: Implementing secure communication protocols, such as Transport Layer Security (TLS) or Secure Sockets Layer (SSL), ensures that data transmitted between systems is encrypted and protected from interception or tampering.
Role-Based Access Control (RBAC): RBAC is a method of access control that assigns permissions and privileges based on the roles and responsibilities of users within an organization. It helps enforce the principle of least privilege, ensuring that users only have access to the resources necessary for their job functions.
Implementing Logical Security Policies
To effectively implement logical security, organizations need to establish comprehensive policies and procedures. These policies should outline the guidelines and best practices for securing digital assets and provide a framework for managing security risks. Some key steps in implementing logical security policies include:
Conducting a Risk Assessment: Organizations should assess their systems and identify potential vulnerabilities and threats. This helps prioritize security measures and allocate resources effectively.
Developing Security Controls: Based on the risk assessment, organizations should develop and implement appropriate security controls. These controls may include encryption mechanisms, access control policies, intrusion detection systems, and regular security updates.
Training and Awareness: Employees play a crucial role in maintaining logical security. Organizations should provide regular training and awareness programs to educate employees about security best practices, such as strong password management, phishing awareness, and data protection.
Regular Audits and Monitoring: Continuous monitoring and periodic audits help identify any security gaps or vulnerabilities. By regularly reviewing and assessing the effectiveness of security controls, organizations can make necessary adjustments and improvements to their logical security measures.
Logic Gates and Logical Security Methods
Logical security methods play a crucial role in safeguarding sensitive information and ensuring the integrity, confidentiality, and availability of data. One of the fundamental components of logical security is the use of logic gates, which are essential building blocks in digital circuits. These gates are employed in various security systems to implement encryption, decryption, access control, authentication, authorization, and other security measures.
Logic Gates in Logical Security Controls
Logic gates are extensively used in logical security controls to enforce security policies and protect computer networks and data. These gates are employed at the gate-level implementation of security systems, where they perform logical operations based on Boolean algebra. By utilizing logic gates, security controls can evaluate the inputs and make decisions to allow or deny access to resources.
In logical security controls, logic gates are often used in conjunction with other security mechanisms such as biometric systems, intrusion detection systems, firewalls, and secure communication protocols. These gates enable the implementation of complex security policies that govern the flow of information and protect against unauthorized access and data breaches.
Logic Gates in Logical Security Policies
Logic gates also play a vital role in the formulation and enforcement of logical security policies. These policies define the rules and regulations that govern access to resources and ensure compliance with information security standards. By using logic gates, security policies can be implemented in a structured and efficient manner.
Logic gates help in the design and evaluation of logical access control policies, which determine who can access specific resources and under what conditions. These gates enable the implementation of authentication and authorization mechanisms that verify the identity of users and grant or restrict their access rights based on predefined rules.
Logic Gates in Logical Access Control
Logical access control is a critical aspect of logical security, and logic gates are integral to its implementation. Logic gates are used to design access control systems that regulate the flow of information within a network and protect against unauthorized access.
By utilizing logic gates, logical access control systems can evaluate user credentials, such as passwords or biometric data, and compare them against predefined rules. These gates enable the implementation of access control policies that ensure only authorized individuals can access sensitive information and resources.
Logic Gates and Decision Making in Security Systems
Role of Logic Gates in Decision Making
Logic gates play a crucial role in decision making within security systems. These gates are fundamental building blocks of digital circuits and are responsible for processing and manipulating binary data. By using Boolean algebra and truth tables, logic gates can evaluate inputs and produce outputs based on specific logical conditions. In the context of security systems, logic gates enable the implementation of various functionalities such as encryption, decryption, access control, authentication, authorization, and more.
In order to understand the role of logic gates in decision making, let’s take a closer look at some common types of logic gates:
AND Gate: The AND gate produces an output of ‘1’ only when all of its inputs are ‘1’. This gate is often used in security systems to implement access control mechanisms. For example, an AND gate can be used to ensure that both a valid access card and a correct PIN are presented before granting access to a restricted area.
OR Gate: The OR gate produces an output of ‘1’ if any of its inputs are ‘1’. In security systems, an OR gate can be used to implement redundancy or backup mechanisms. For instance, an OR gate can be employed to activate an alternative power source in case the primary power supply fails.
NOT Gate: The NOT gate, also known as an inverter, produces the logical complement of its input. It converts ‘1’ to ‘0’ and ‘0’ to ‘1’. In security systems, a NOT gate can be used to invert a signal, which can be useful for various purposes such as intrusion detection or triggering an alarm when a specific condition is not met.
How Logic Gates Influence Security Decisions
Logic gates have a significant influence on security decisions within various systems. By combining different logic gates, complex decision-making processes can be implemented. This allows security systems to evaluate multiple inputs and make informed decisions based on predefined rules and conditions.
For example, in the context of biometric systems, logic gates can be used to compare the captured biometric data with stored templates. By utilizing logic gates, the system can determine whether the captured data matches the stored data, enabling authentication or access control.
Furthermore, logic gates are essential in the design and implementation of intrusion detection systems and firewalls. These systems rely on logic gates to analyze network traffic and identify potential threats or unauthorized access attempts. By evaluating the inputs received from various sensors and analyzing patterns, logic gates can trigger appropriate actions to mitigate potential risks.
Logic Gates and Gatekeeper ICT Decisions
In the realm of information security and computer networks, logic gates play a crucial role in gatekeeper ICT decisions. Gatekeepers are responsible for controlling access to resources and ensuring the security of sensitive data. Logic gates enable gatekeepers to make decisions based on predefined rules and conditions, allowing or denying access to specific resources.
For instance, when it comes to secure communication, logic gates can be used to implement encryption and decryption algorithms. By utilizing logic gates, sensitive information can be encoded and decoded, ensuring confidentiality and data protection during transmission.
Moreover, logic gates are utilized in the design and implementation of firewalls, which act as gatekeepers for computer networks. Firewalls use logic gates to evaluate incoming and outgoing network traffic, applying predefined rules to allow or block specific connections. This helps in preventing unauthorized access and maintaining the security of the network.
The Future of Logic Gates in Security Systems
In the rapidly evolving world of technology, logic gates play a crucial role in ensuring the security of various systems. Logic gates are fundamental building blocks of digital circuits, enabling complex operations such as encryption, decryption, access control, authentication, and authorization. As the demand for secure systems continues to grow, the future of logic gates in security systems holds great promise.
Logic Locking and EDA Tools
Logic locking is a technique that enhances the security of logic gates by introducing additional functionality that can only be unlocked with a specific key. This approach provides an extra layer of protection against unauthorized access and tampering. Electronic Design Automation (EDA) tools are essential in implementing logic locking techniques, allowing designers to create secure circuits efficiently.
Advancements in EDA tools have made logic locking more robust and effective. These tools provide designers with a wide range of options to implement logic locking, including different locking mechanisms and key generation algorithms. By leveraging these advancements, security professionals can enhance the resilience of logic gates in security systems.
Advancements in Logic Gate Security Systems
The future of logic gates in security systems is not limited to logic locking alone. Researchers and engineers are continuously exploring new ways to improve the security of logic gates and their applications. Some of the key advancements in logic gate security systems include:
Biometric Systems: Integrating biometric authentication with logic gates adds an extra layer of security. Biometric systems, such as fingerprint or iris scanners, can be used to authenticate users before granting access to sensitive information or resources.
Intrusion Detection and Firewalls: Logic gates can be utilized in intrusion detection systems and firewalls to monitor network traffic and identify potential threats. By analyzing patterns and behaviors, these systems can detect and prevent unauthorized access or malicious activities.
Secure Communication: Logic gates play a vital role in ensuring secure communication between devices and networks. Techniques such as encryption and decryption, implemented using logic gates, protect sensitive data from unauthorized interception or tampering.
Information Security in Computer Networks: Logic gates are essential in securing computer networks by implementing various security protocols. They enable functions such as data protection, access control, and secure data transmission, ensuring the confidentiality and integrity of information.
Potential Challenges and Solutions
While the future of logic gates in security systems is promising, there are also challenges that need to be addressed. Some of the potential challenges include:
Complexity: As security requirements become more stringent, the complexity of logic gate implementations increases. Designers need to find a balance between security and performance to ensure efficient and effective security systems.
Vulnerabilities: Logic gates themselves can be vulnerable to attacks, such as side-channel attacks or hardware Trojans. Researchers and designers need to continuously identify and mitigate these vulnerabilities to maintain the integrity of security systems.
Integration: Integrating logic gates into existing systems or designing new systems with security in mind can be a complex task. Collaboration between security experts, hardware designers, and software developers is crucial to ensure seamless integration and optimal security.
To overcome these challenges, collaboration between academia, industry, and government organizations is essential. Continuous research and development in the field of logic gates and security systems will pave the way for innovative solutions and robust security measures.
How have logic gate innovations in manufacturing impacted the security systems?
Logic gate innovations in manufacturing have had a significant impact on the development and functionality of security systems. By integrating advanced logic gates, security systems can be more efficient in detecting and preventing unauthorized access or breaches. These innovations have paved the way for the creation of complex and robust security algorithms that can analyze data inputs and make real-time decisions, enhancing the overall security measures. For more information on logic gate innovations in manufacturing, you can visit “Logic gate innovations in manufacturing”.
Frequently Asked Questions
1. What is logical security?
Logical security refers to the measures and methods used to protect computer systems and data from unauthorized access, ensuring the confidentiality, integrity, and availability of information.
2. How do logic gates work?
Logic gates are electronic circuits that perform basic logical operations, such as AND, OR, and NOT, based on Boolean algebra. They process binary inputs and produce binary outputs according to predefined truth tables.
3. What are logic gates used for in real life?
Logic gates are fundamental building blocks of digital circuits and are used in various real-life applications, including computer processors, calculators, traffic light control systems, and even in everyday electronic devices like smartphones and televisions.
4. What is the role of security systems in information security?
Security systems, such as firewalls, intrusion detection systems, and biometric access control, play a crucial role in safeguarding computer networks and data from unauthorized access, attacks, and other security threats.
5. How does encryption contribute to information security?
Encryption is a process of converting plain text into ciphertext using an encryption algorithm and a secret key. It helps protect sensitive information by making it unreadable to unauthorized individuals, ensuring confidentiality.
6. What is the difference between authentication and authorization?
Authentication is the process of verifying the identity of a user or system, while authorization involves granting or denying access rights and permissions to authenticated users based on their roles and privileges.
7. How do biometric systems enhance access control?
Biometric systems use unique physical or behavioral characteristics, such as fingerprints, iris patterns, or voice recognition, to verify the identity of individuals. They provide a more secure and reliable means of access control compared to traditional methods like passwords or ID cards.
8. What are logical security controls examples?
Logical security controls include measures like user authentication, password policies, access control lists, encryption, intrusion detection systems, and logical toegangsbeveiliging application control, among others.
9. How is logical security implemented?
Logical security is implemented through a combination of technical measures, such as firewalls, encryption, and access control systems, as well as organizational policies, procedures, and user awareness training.
10. Does logic locking work with EDA tools?
Yes, logic locking is a technique used to protect intellectual property in integrated circuits. It involves adding additional logic gates to the design, making it difficult for unauthorized users to reverse-engineer or tamper with the circuit using Electronic Design Automation (EDA) tools.
Also Read:
- Logic gate packaging considerations
- Numeric problems on logic gate capacitance
- How to replace a malfunctioning logic gate
- Logic gate overvoltage problems
- Logic gate response time
- Logic gate latency issues
- Numeric problems on logic gate speed
- Logic gate derivatives
- Implications of logic gate failures in systems
- Logic gate fanout calculation problems

The TechieScience Core SME Team is a group of experienced subject matter experts from diverse scientific and technical fields including Physics, Chemistry, Technology,Electronics & Electrical Engineering, Automotive, Mechanical Engineering. Our team collaborates to create high-quality, well-researched articles on a wide range of science and technology topics for the TechieScience.com website.
All Our Senior SME are having more than 7 Years of experience in the respective fields . They are either Working Industry Professionals or assocaited With different Universities. Refer Our Authors Page to get to know About our Core SMEs.
